Consumerization of IT (CoIT) is a reality to many organizations today. Employees more and more want to use their personal electronic devices to do their jobs, and utilize the same technologies and applications at work that they use at home. This blending of consumer and enterprise technologies is the Consumerization of IT, and it boosts employee productivity and satisfaction. However, it can make it difficult for IT departments to ensure an enterprise’s data security and integrity. Many people think CoIT is only about “Devices Management”. To have a successful CoIT strategy, we also need to think about People, Security and Management, , and Productivity**.** Microsoft IT built the support for CoIT based on following four pillar.  • Windows PCs and other devices: Classify what are enterprise-standard, consumer-standard, and nonstandard devices, and then determine the various support models for each. Look at your support model, think about how difference devices will be supported and what level of support each kind of devices gets. • Security and management: Determine how to manage and control these devices, and their users’ access to intellectual property, and then ensure data’s integrity and security once users place it on these devices. Different people may handle different information, HR and Finance Department typically handle more sensitive data and information. Classify different data and information then build access and control polices around it. For example, highly business impact (Like HR and Finance records) data and information should be only accessed from managed devices. Low business impact data and information may be accessed through unmanaged devices to enable flexibility. • Productivity: Determine which applications and technologies to support on employees’ devices to ensure that they continue to be satisfied and productive. •Unified application development: Establish best practices for line-of-business (LOB) application development, and ensure a secure development lifecycle and marketplace for these applications Below table (Click to enlarge) illustrate how Microsoft IT support Bring Your Own Device (BYOD) for both Windows and Non-Windows Devices. It also shows what kind of access each device can get.
• Windows PCs and other devices: Classify what are enterprise-standard, consumer-standard, and nonstandard devices, and then determine the various support models for each. Look at your support model, think about how difference devices will be supported and what level of support each kind of devices gets. • Security and management: Determine how to manage and control these devices, and their users’ access to intellectual property, and then ensure data’s integrity and security once users place it on these devices. Different people may handle different information, HR and Finance Department typically handle more sensitive data and information. Classify different data and information then build access and control polices around it. For example, highly business impact (Like HR and Finance records) data and information should be only accessed from managed devices. Low business impact data and information may be accessed through unmanaged devices to enable flexibility. • Productivity: Determine which applications and technologies to support on employees’ devices to ensure that they continue to be satisfied and productive. •Unified application development: Establish best practices for line-of-business (LOB) application development, and ensure a secure development lifecycle and marketplace for these applications Below table (Click to enlarge) illustrate how Microsoft IT support Bring Your Own Device (BYOD) for both Windows and Non-Windows Devices. It also shows what kind of access each device can get. 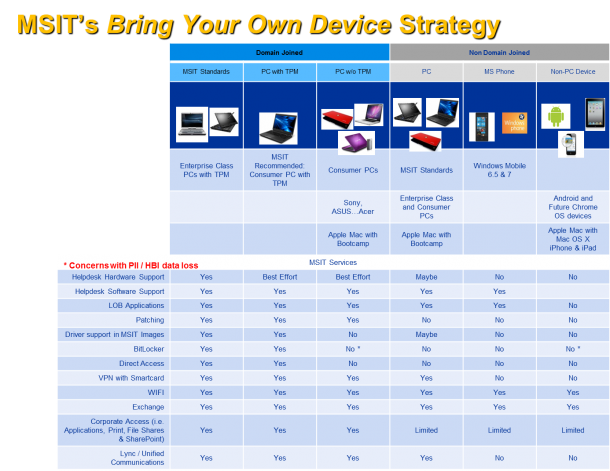 Here is list of technologies that involved to build this approach.
Here is list of technologies that involved to build this approach.
- Active Directory
- Exchange Active Sync
- System Center Configuration Management 2012
- IPSec policies to control access to your most secure resources
- Network Access Protection – to ensure minimum standards
- A modern gateway – to present secure web access to internal resources
- Firewalls
- Remote Desktops and VDI – to provide a consistent fall back environment, or secure remote access
- DirectAccess
- App-V – to deliver virtual applications so that you can remove them easily when no longer needed
Let me know your thoughts around CoIT, simply just leave comments!