Welcome to a blog series about Windows Server 2012. Recently many people asked me about what are the exciting things about Windows Server 2012 apart from Virtualization. Well, there are many of them. One thing probably left in the shadow of the over 375 new features is IIS 8.0. Let’s look at what are the improvements. Why do i care abou these new features? Here is a table how IIS 8.0 in Windows Server 2012 can address some challenges today.
Welcome to a blog series about Windows Server 2012. Recently many people asked me about what are the exciting things about Windows Server 2012 apart from Virtualization. Well, there are many of them. One thing probably left in the shadow of the over 375 new features is IIS 8.0. Let’s look at what are the improvements. Why do i care abou these new features? Here is a table how IIS 8.0 in Windows Server 2012 can address some challenges today. 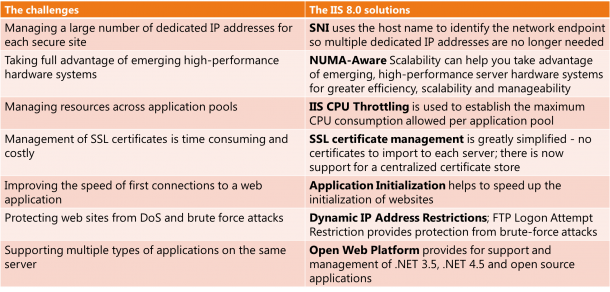 Let’s dive into each one of them
Let’s dive into each one of them
Server Name Indication (SNI): SSL Scalability
Server Name Indication (SNI) uses a virtual domain name to identify a network endpoint, eliminating the need to have a dedicated IP address for each secure site. It does this by extending the Transport Layer Security (TLS) protocol to include the virtual domain name during Secure Sockets Layer (SSL) negotiation. SNI allows the client to request the domain name before the certificate is committed to the server. With SNI, a host name can be used along with IP address and port to identify the network endpoint, eliminating the need to have a dedicated IP address for each secure site. In the past, if you had 10,000 tenants, you would need 10,000 unique IP addresses. With SNI, you need only one. SNI also supports thousands of SSL certificates and uses the local certificate store. The new Web Hosting store works like the Personal store, so all of the existing tools to import and export certificates work the same way. The key difference between Web Hosting store and Personal store is that Web Hosting store is designed to scale to higher numbers of certificates. 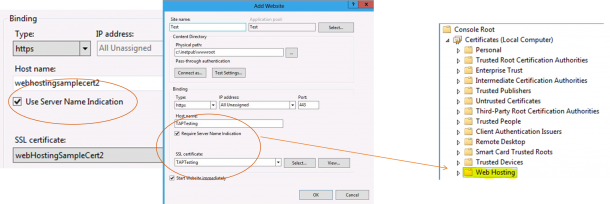 Here is a Step by Step Guide
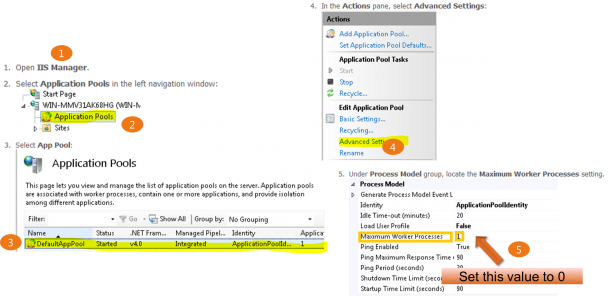
Here is a Step by Step Guide
Multicore Scaling on NUMA Hardware
Generally speaking, increasing the number of cores should result in increased performance. However, there comes a point where increasing the number cores may result in performance degradation because the cost of memory synchronization out-weighs the benefits of additional cores. IIS 8 addresses this problem by intelligently distributing and affinitizing its processes on Non-Uniform-Memory-Access (NUMA) hardware. Internet Information Services (IIS) on Windows Server 8 is NUMA-aware and provides the optimal configuration for the IT administrators. Efficiency
- Provides a high return on hardware investments
- Takes advantage of an increased number of processor cores
- Runs web applications more efficiently on the same resources (see chart)
Scalability
- Divides the workload into multiple processes and uses NUMA nodes to minimize the need for the CPU to synchronize memory across servers
Manageability
Here is a Step by Step Guide
CPU Throttling: Sand-boxing Sites and Applications
In a multi-tenanted deployment, such as a shared hosting environment, it is important to create a sand-box for each tenant. Without the sand-box, a tenant could intentionally or unintentionally impact other tenants negatively by accessing other tenants’ contents or by monopolizing resources, such as memory, CPU, and bandwidth. On IIS 8.0, CPU Throttling enables customers to truly limit how much CPU each tenant can consume as a percentage of CPU. Furthermore, this feature is configurable per IIS application pool, which means each tenant could have different limits, which can lead to a new business model in which tenants can pay more for higher limits. It is important to clarify that IIS CPU Throttling is not a reservation of a CPU resource. Rather it is a way to limit the maximum usage. It is important to clarify that IIS CPU Throttling is not a reservation of a CPU resource. Rather it is a way to limit the maximum usage. 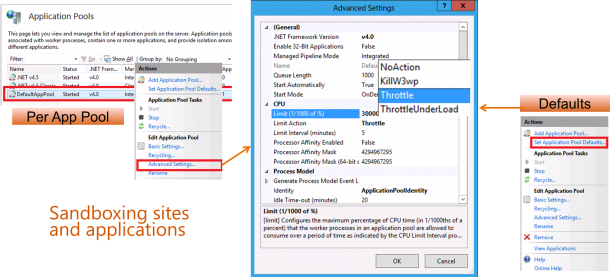 Here is a Step by Step Guide
Here is a Step by Step Guide
Centralized SSL Certificate Support: SSL Scalability and Manageabilit****y
In the past, if you had 20 servers in a server farm, you would have to copy and import SSL certificates on all 20 computers, one by one. The problem increases exponentially if you have 10,000 tenants that all want a secure site. The result is 10,000 SSL certificates that have to be copied to all 20 computers and imported individually. The Centralized SSL Certificate Support feature in Windows Server 2012 is used to store all SSL certificates centrally in a file server, where they are shared by all servers in the server farm. In the preceding example, the 20 computers get the SSL certificates from a central location so the administrator has just one location to update the certificate. Additionally, there is no need for any special “importing” procedure—To configure a new server, you simply point to the file server with SSL certificates 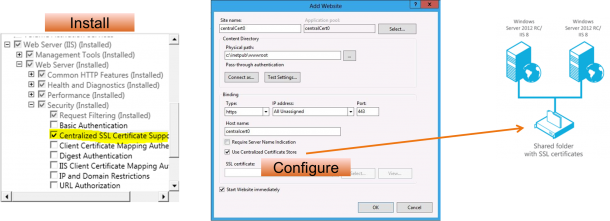 Here is a Step by Step Guide
Here is a Step by Step Guide
Application Initialization
The IIS 8.0 Application Initialization feature enables website administrators to configure IIS 8.0 to proactively perform initialization tasks for one or more web applications. While an application is being initialized, IIS 8.0 can also be configured to return static content as a placeholder or “splash page” until an application has completed its initialization tasks. The Application Initialization feature is configured through a combination of global and application-specific rules that tell IIS 8.0 how and when to initialize web applications. The Application Initialization feature also supports integration with the IIS Url Rewrite Module to support more complex handling of placeholder content while an application is still initializing. 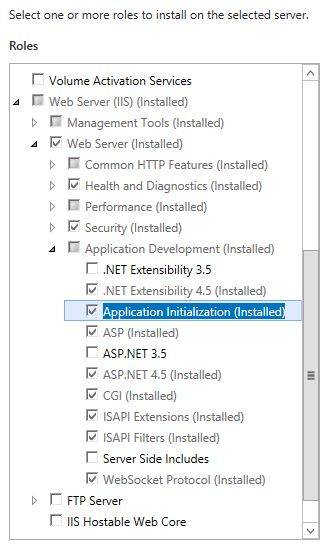 Example modifications in applicationHost.config Application pool configuration entry:
Example modifications in applicationHost.config Application pool configuration entry:
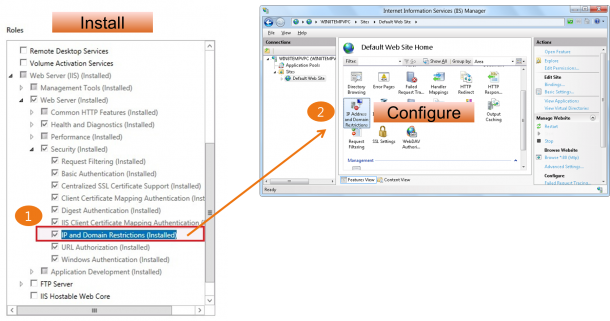
Dynamic IP Address Restrictions
IIS 7 and earlier versions had built-in functionality that allowed administrators to allow or deny access for individual IP addresses or ranges of IP addresses. When an IP address was blocked, any HTTP clients from that IP address would receive an HTTP error “403.6 Forbidden” reply from the server. This functionality allowed administrators to customize the access for their server based on activity that they see in their server’s logs or website activity. However, this is a manual process. Even though functionality can be scripted to discover malicious users by examining the IIS log files by using a tool like Microsoft’s LogParser utility, this still requires manual intervention. IIS 8.0 for Windows Server 2012 allows you to easily set up filters to automatically deny access based on criteria that you can determine based on your security needs. This feature’s primary benefit is to protect servers from DoS attacks by automatically blocking potentially harmful IP addresses. In IIS 8.0, Microsoft has expanded the built-in functionality to include several new features:
- Dynamic IP address filtering, which allows administrators to configure their server to block access for IP addresses that exceed the specified number of requests.
- The IP address filtering features now allow administrators to specify the behavior when IIS blocks an IP address, so requests from malicious clients can be aborted by the server instead of returning HTTP 403.6 responses to the client.
- IP filtering now feature a proxy mode, which allows IP addresses to be blocked not only by the client IP that is seen by IIS but also by the values that are received in the x-forwarded-for HTTP header
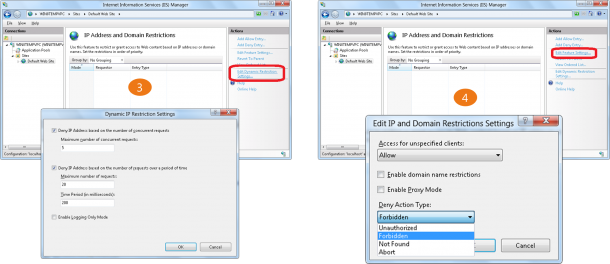
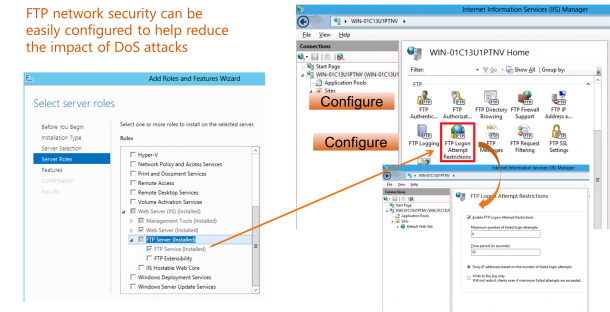 Here is a Step by Step Guide
Here is a Step by Step Guide
What is next:
Download and try out Windows Server 2012: http://aka.ms/winsrv2012