When comes to public cloud like Windows Azure, security is always a popular area for many customers. A new technical whitepaper on Windows Azure Network Security is released to help IT Administrator to understand the security mechanisms within Windows Azure. Windows Azure networking provides the infrastructure necessary to securely connect your virtual machines to one another, as well as bridge between the cloud and your on-premises datacenter
Few of the questions I get asked a lot are around protection against DDOS and intrusion detection. The whitepaper explains those points in detail.
|
Protecting against DDOS |
Windows Azure has a distributed denial-of-service (DDoS) defense system that helps prevent attacks against Windows Azure platform services. It uses standard detection and mitigation techniques such as SYN cookies, rate limiting, and connection limits.Windows Azure’s DDoS defense system is designed not only to withstand attacks from the outside, but also from within.
Windows Azure’s DDoS protection also benefits applications. However, it is still possible for applications to be targeted individually. As a result, customers should actively monitor their Windows Azure applications. For more information, see Collect Logging Data by Using Windows Azure Diagnostics.
If a customer notices their application is under attack, they should contact Windows Azure Customer Support to receive assistance. Windows Azure Customer Support personnel are trained to react promptly to these types of requests.
|
|
|
Intrusion detection and prevention |
Certain appliances such as Web Application Firewalls (WAF) can proxy communications by terminating and then forwarding the traffic to endpoints, also applying intrusion detection and prevention, as well as denial of service mitigation techniques. Virtual appliance form-factors should work on Windows Azure as long as they are certified by the vendor to do so. |
The whitepaper also gives insights on how customers can take advantage of the platform’s native features to best protect their information assets.
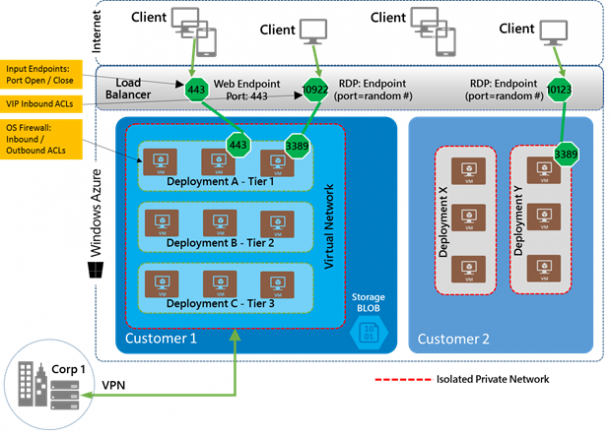
Figure 1. An example of isolated multi-tier IaaS applications hosted within Windows Azure.

 Follow
Follow