We recently concluded the Microsoft Student Partners 2016 registration exercise, but what most people didn’t catch is that the website was full of Easter eggs and puzzles. Let me walk you through the backstage.
For this year’s MSP recruitment, Microsoft reached out to a much larger student audience than we’ve ever handled. That meant we needed to implement some form of “noob filter”, taking the form of the 4 main questions:
- A developer’s first app is commonly a Hello _____ app.
- Microsoft recently announced a free new way to create Windows, Android, and iOS apps in C#. What is the name of that tool?
- Right out of Star Wars, what’s that awesome new product that brings holograms to life?
- Find the hidden password on this page.
Questions 1-3 are fairly simple, and the answers are “world”, “xamarin”, and “(microsoft) hololens” respectively. Capitalization doesn’t matter, and a whole bunch of different ways to input “HoloLens” are handled.
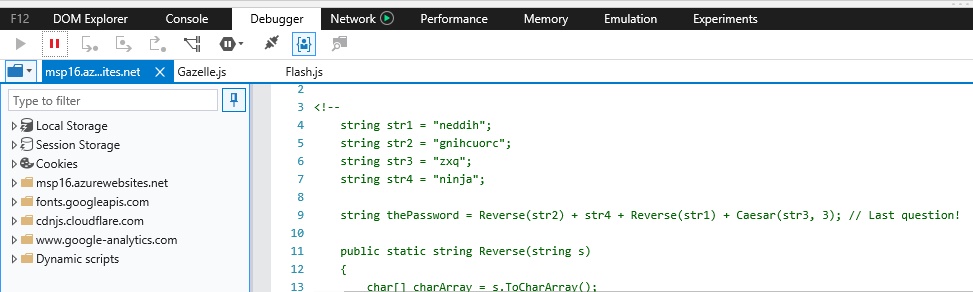 The hidden password for Question 4 could be derived from a puzzle within the website’s source code. It’s a simple C# puzzle that could be solved without an IDE, but there were a number of people who:
The hidden password for Question 4 could be derived from a puzzle within the website’s source code. It’s a simple C# puzzle that could be solved without an IDE, but there were a number of people who:
- Ignored the warnings when launching the website, and couldn’t do anything on mobile
- Did not know to look in the source code (the majority of people who asked for hints)
- Copy and pasted the code into Visual Studio, then ran it
- Got the order of the puzzle wrong resulting in the wrong “password”
- And my personal favorite, finding every other Easter egg on the page and not finding the actual password (???)
That being said, there were 12 Easter eggs in the website on top of the 4 main questions. They’re set up in the style of (a very basic) Capture the Flag (which would make this the CTF writeup). Hitting the Information button at the bottom left of the page opens a dialog box with an egg at the side, which links to a checklist on OneDrive (they are listed in order of development):
- Main Question 1 reminds us it’s a small world after all.
- Main Question 2 tells us that the best things in life are free!
- Main Question 3 envisions the possibilities of teleportation… Kinda.
- And Main Question 4, neatly tucked away under the surface… But is there anything deeper?
- One of these are not like the other.
- One of them was in fact too yucky to execute.
- But I must comment that anyone can be anything.
- Also, these aren’t the robots you’re looking for. Speaking of robots, are they leaking anything?
- Perhaps a box in a box?
- And many homes in that box?
- Hey box sounds like fox, do they communicate via mor-mor-mor-mor-morse?
- Well, sometimes the clue is in the name.
- Layered security’s good practice, and with it – obscurity!
- Never scold your developer – watch your language!
- Don’t think so much.
- And finally, this website was brought to you by the letter M.
If you want to try your hand, the website is still up (as of this post). If not, here’s the walkthrough.
5. One of these are not like the other.
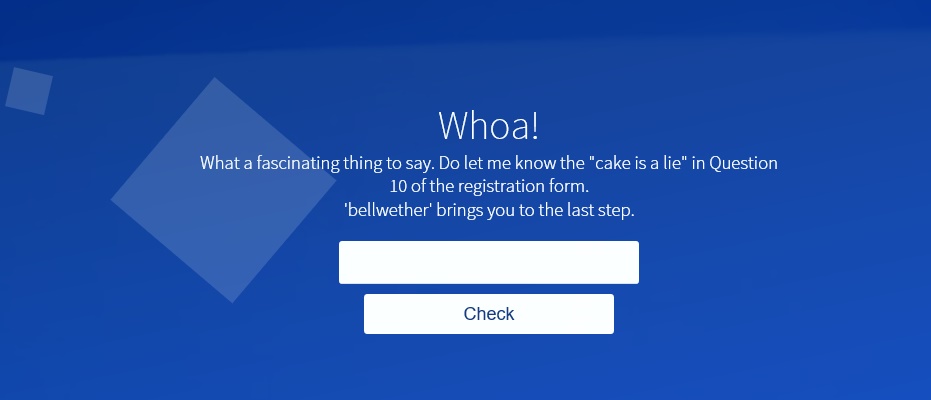 The bubbles that move on the page are actually <li> elements. One such element has an <a> tag attached to it, displaying a pop-up with a keyword “thereisnocowlevel” that can be entered to get a flag (phrase) to be entered later on in the registration process.
The bubbles that move on the page are actually <li> elements. One such element has an <a> tag attached to it, displaying a pop-up with a keyword “thereisnocowlevel” that can be entered to get a flag (phrase) to be entered later on in the registration process.
This was also the first egg developed, and is the only one that doesn’t end with a Zootopia reference. There were quite a few people that thought this was the hidden password for Question 4, resulting in a loop. One of my testers simply launched the onclick function in his browser’s Developer Console, so I had to add extra protection. Which leads us to the next puzzle…
6. One of them was in fact too yucky to execute.
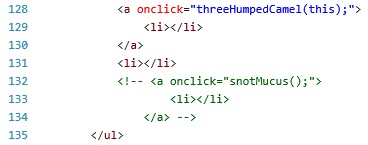 Just below there is another <li> element that is commented out. It has another onclick function that can easily be executed from Developer Console, opening a .txt file with an MD5 hash. Decrypting and entering it into the website would yield another flag.
Just below there is another <li> element that is commented out. It has another onclick function that can easily be executed from Developer Console, opening a .txt file with an MD5 hash. Decrypting and entering it into the website would yield another flag.
7. But I must comment that anyone can be anything.
There are two more comment blocks at the bottom of the page. The bottom one talks about “my new favorite show whose name can be entered“, and “That show is © Disney“. Entering ‘Zootopia’ changes the answer box to ‘tryEverything();’, which, when entered into Developer Console, pops up a flag and changes the background video to Try Everything by Shakira.
8. Also, these aren’t the robots you’re looking for. Speaking of robots, are they leaking anything?
The comment block above that simply states “Search bots should be looking for a different txt file“. Navigating to /robots.txt gives another flag in comments at the top of the page. Two directories are also listed – /cityhall/ and /files/.
9. Perhaps a box in a box?
 Navigating to /files/ shows a fake Apache file directory with 3 files – “box”, “dots.mp3”, and “hex.jpg”. Opening “box” in a hex editor shows the .zip file signature (PK), and opening the file as such will provide a .txt file with SSH credentials. Of course, there are many ways of getting to this step (e.g. guessing file extension, using strings to list all text).
Navigating to /files/ shows a fake Apache file directory with 3 files – “box”, “dots.mp3”, and “hex.jpg”. Opening “box” in a hex editor shows the .zip file signature (PK), and opening the file as such will provide a .txt file with SSH credentials. Of course, there are many ways of getting to this step (e.g. guessing file extension, using strings to list all text).
Entering those credentials into an SSH client will log a user into a Linux environment hosted on Microsoft Azure with another flag as the motd (message of the day).
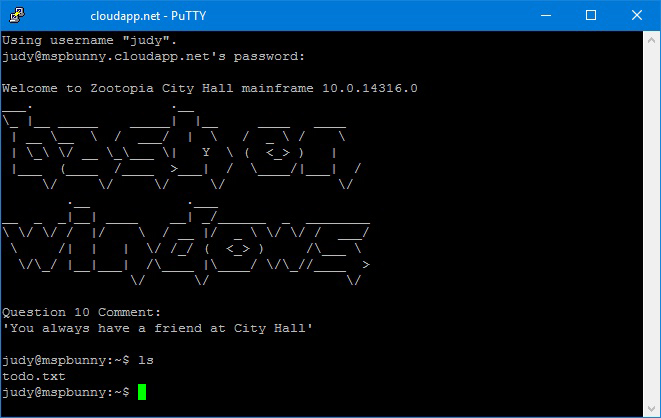
10. And many homes in that box?
There’s a text file in the account (~judy)’s home that, when read, asks the user to find out what other accounts are on the server. Using “cat /etc/passwd“, another account is revealed along with its password. A file in that account (~nick)’s home has another phrase that when entered on the website provides another flag.
11. Hey box sounds like fox, do they communicate via mor-mor-mor-mor-morse?
“dots.mp3” is just morse code. Just played really fast. The 12 character translation will yield another flag when entered on the website.
12. Well, sometimes the clue is in the name.
As for “hex.jpg“, there’s extra text at the bottom of the file that can also be entered on the website for a flag.
13. Layered security’s good practice, and with it – obscurity!
Now we’re on to /cityhall/. The first page’s clue is “Hah, they won’t be able to attack what they can’t see…“. Open Developer Console, edit the form and find a hidden input set to false. Changing that to true will let you through.
14. Never scold your developer – watch your language!
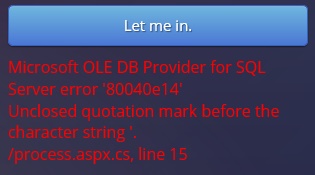 Second page’s clue is “And they definitely can’t burn through my fool-proof super short password checking code!“. Trying to input an apostrophe will result in an SQL error regarding an unclosed quotation mark – this input is SQL Injectable. Doing something like “‘ OR 1=1” would move the user to the next page.
Second page’s clue is “And they definitely can’t burn through my fool-proof super short password checking code!“. Trying to input an apostrophe will result in an SQL error regarding an unclosed quotation mark – this input is SQL Injectable. Doing something like “‘ OR 1=1” would move the user to the next page.
Interestingly – this is all completely hardcoded. One of the testers talked about DDoSing the page by spamming SQL transactions, he was pretty surprised when I told him there wasn’t any SQL server.
15. Don’t think so much.
Third page’s clue is “I suppose having something weak once in a while is okay, since there are so many layers…“. Entering the weak password “123456” moves to the next and final stage.
16. And finally, this website was brought to you by the letter M.
My manager said no one would understand this clue. Sesame Street! Cookie Monster, get it? Get it? D:
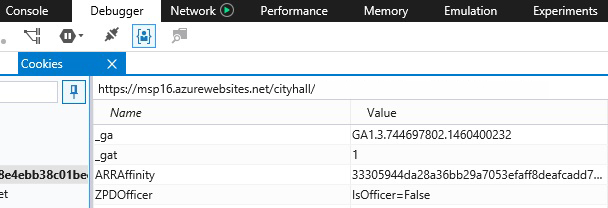
The clue is “Maybe we’ll even use another way of identifying authorized personnel!“. Use your browser’s Developer Console or plugin (depending on your browser, although Microsoft Edge seems to have the best implementation of this, seriously), edit the cookies for the page and flip “IsOfficer” to “True“. Move to the end page for eye candy.
This year’s MSP recruitment is over, and we’ve had an unprecedented record number of applicants. Should you wish to play with the website, it’ll remain up indefinitely. Thanks for reading, and thank you for supporting Microsoft – where we provide free professional tools and services to students so that anyone can be anything! 🙂
P.S. As internal gags, “goodjason” and “badjason” do have effects as well.
Need to contact the MSP Singapore Team? Reach us here.

 Follow
Follow